
Claims-aware apps perform a redirection to the Security Token Service (STS). The STS requests credentials from the user in exchange for a token and then redirects the user to the application. There are a few ways to enable application proxy to work with these redirects. Use this article to configure your deployment for claims-aware apps.
The STS that the claims-aware app redirects to must be available outside of your on-premises network. Expose it through a proxy or by allowing outside connections.
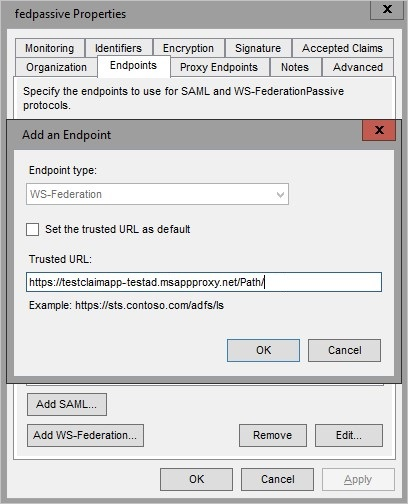
You can configure Active Directory Federation Services for claims-aware apps in one of two ways. The first is by using custom domains. The second is with WS-Federation.
If all the internal URLs for your applications are fully qualified domain names (FQDNs), then you can configure custom domains for your applications. Use the custom domains to create external URLs that are the same as the internal URLs. When your external URLs match your internal URLs, then the STS redirections work whether your users are on-premises or remote.

